"
Hello,
Attached are the Investment Reports, Real Estate Updates, government Reports, and new developments for our upcoming events.
This information is strictly meant for Spokane County 2018 Elected PCO's Members
We are pleased to bring this information to you in a secure manner via our partners, Google Drive Secured.
Have a nice day.
And indeed, when the Inlander tried to forward the message to Stephen Heath, vice president of security for Intrinium, a local IT consulting firm, their system automatically booted back the message, having identified a "Malicious Payload."
The Spokane County Democrats put out a warning on Facebook last night:
"DO NOT OPEN THE ATTACHMENT! If you have already opened the attachment, we strongly recommend running quality anti-malware software on your computer immediately. Malwarebytes (https://www.malwarebytes.com/) is a well-respected and high quality option recommended by our tech officer.The Inlander was also alerted to the phishing attack by a local Republican precinct committee officer. The attack appears to have been farmed from the email addresses listed from this public PDF at the Spokane County website.
"There’s a tool called the social engineering toolkit, you can clone a site with it pretty much trivially," Heath says. "They might be using something like that to do it."
The email twice uses the phrase "Spokane County 2018 Elected PCO's" in exactly the same format as the PDF at the Spokane County website does.
"It feels like it’s a very broad-net kind of thing," Heath says. "They would do a search for Gmail addresses then did a mass attack against anybody."
He says it didn't look it was something that was trying to target any one group in a sophisticated way.
"Then again the John Podesta thing was just, ‘Hey, can you rest your Gmail password?'” Heath says.
Heath says that phishing attacks — where hackers trick you into giving up your username, password, or other personal information by having you enter the information into a fake site — have become increasingly common. Both software and users have become
"It’s a lot easier to get people to click a link," Heath says. After all, a lot of security software more carefully scrutinizes traffic that's coming into a network than traffic going out.
So what happens if people
And if people clicked that red "VIEW INFORMATION" link below?
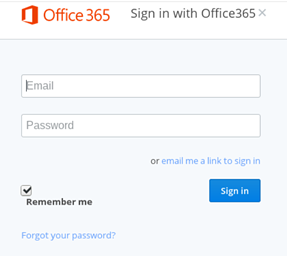
Heath booted up a virtual machine to ensure he could investigate it without infecting his computer. He says the link sends you to a login page where you can supposedly "login" to a variety of accounts, from Gmail, to Office 365, to Yahoo
"Click any one of these things, it's giving you a login page for whatever you'd expect," Heath says.
Type in any information into that, and it takes you to a Google Docs message that the item you'd tried to access had violated the site's terms of service.
"They’re trying to copy the username and password into somewhere into Google's [backend]" Heath says. "I’m guessing they’re just trying to abuse something in Google to grab it."
The IP address of the site is from Amsterdam, Heath says. But that doesn't necessarily mean that's where the hacker is located — just where the site is hosted.
"That particular site isn't on any of the blacklists," Heath says. "So it's something that was spun up fairly recently."
Spokane County spokesman Jared Webley says there's no indication that any other email list on the Spokane County website has been targeted and emphasizes that the Spokane County IT department regularly conducts training to inoculate their staff against common phishing attacks.
But even the most sophisticated users can become victims. Even Heath was successfully phished early this year. He was a victim of bad timing. Right after hanging up the phone with one of his partners he got an email with the invoice from that partner.
Without even thinking, he says, he clicked.
"It can happen to anyone," Heath wrote in a blog post. "Just because you are 'smart' and have 'security' in your title does not make you automatically immune."
So what should you do if you accidentally get tricked? Obviously, change your password. Turn on two-factor authentication, requiring you to confirm using your phone whenever you're trying to sign in at an unusual time or location.
And if you have a smartphone, you might just want to completely reset the phone and start over.
"All the training is don't click, don't click, don't click, but nobody focuses on what happens if you do," Heath says.